Let’s Talk Phishing—Part 3: When Scammers Pose as XMission
They’re getting smarter: Phishing attacks are now targeting XMission’s identity
 Over the past several months, we’ve seen a dramatic rise in phishing emails targeting XMission customers. Not from random overseas scam operations, but from threat actors who are mimicking XMission’s branding, tone, and even our past support language.
Over the past several months, we’ve seen a dramatic rise in phishing emails targeting XMission customers. Not from random overseas scam operations, but from threat actors who are mimicking XMission’s branding, tone, and even our past support language.
These aren’t your typical typo-riddled scams. They use our logo, our formatting, and our language. And they’ve been hitting inboxes with alarming frequency.
We want to pull back the curtain on what we’re seeing, why it’s happening, and what you can do to protect yourself.
Phishing that looks like it came from us
Below are real examples of phishing emails we’ve received reports of. The formatting and phrasing may seem familiar, but the links are not. These emails are not from XMission and should be treated as malicious.
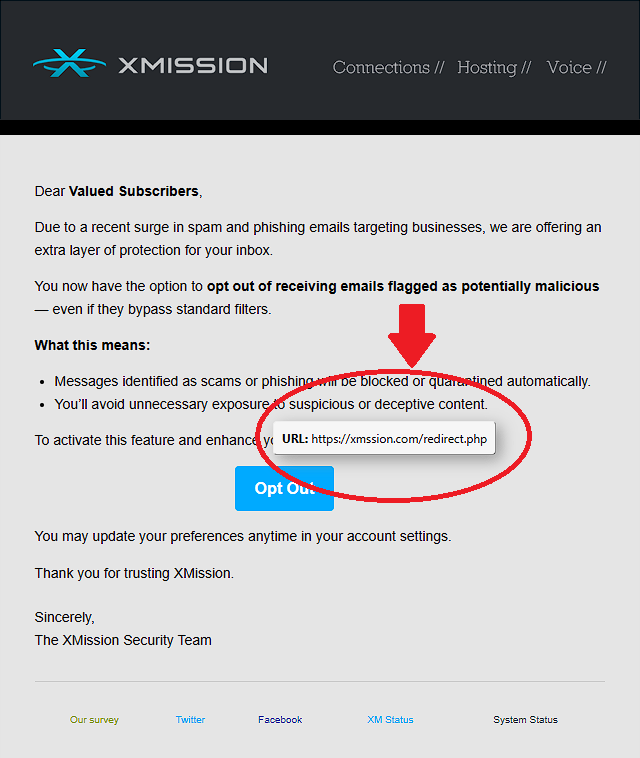
“Notice: New Policy for Handling Suspicious Messages” (Spoofed Support Notice)
This email appears to offer additional security services, using language like “opt out of receiving flagged emails.” It includes a very convincing button with the familiar XMission blue.
What’s wrong with it?
- The link behind the “Opt Out” button points to a fake domain:
https://xmssion.com/redirect.php– note the subtle typo in the domain name. - The tone mimics our security notices but includes no specific account or login references.
- XMission never updates your preferences via a single-click email action.
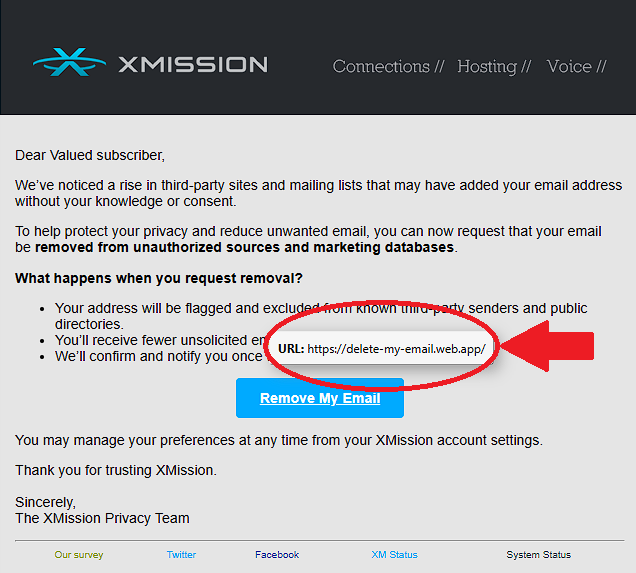
“Mandatory Privacy Notice: Email Removal Option Now Available” (Privacy Bait)
This phishing attempt plays on privacy concerns. It offers to remove your address from marketing databases, using familiar opt-out language and visual styles.
What’s wrong with it?
- The link behind “Remove My Email” points to
https://delete-my-email.web.app/– which is not owned or affiliated with XMission. - While it sounds helpful, it’s likely a credential harvester or malware site.
- Legitimate unsubscribe or privacy options will always route through the xmission.com URLs.
Why target XMission?
We’ve asked ourselves this too. XMission is a regional ISP and hosting provider, not a global tech giant. So why the escalation in phishing campaigns against us and our users?
Our best speculations:
- We’re one of the few providers that actively fight back. XMission has taken legal action against spammers in the past. That kind of stance makes us a target.
- Our users trust us. Our brand carries weight with our customers. That trust is exactly what phishers try to exploit by mimicking our brand.
Regardless of motive, the outcome is clear: XMission users are receiving deceptive, targeted emails that attempt to exploit their relationship with us.
How to spot these attacks:
- Hover before you click. Look closely at URLs. Does it say “xmission.com” or a typo version?
- Be wary of urgency. Anything saying “click now” to avoid account shutdown or data loss should raise red flags.
- Check for generic language. Legitimate messages from us typically reference your account or specific service.
- Never trust buttons blindly. If you’re unsure, log into your control panel directly at xmission.com instead.
- Report it. Forward suspicious messages to spam@xmission.com so we can investigate and take appropriate action.
- Trust your spam folder. If a message says it’s from XMission but landed in your junk/spam folder, there’s probably a good reason.
Enable security features
If you’re using Zimbra webmail, here are two things you can do right now to strengthen your account security:
- Enable Two-Factor Authentication (2FA): Go to your account settings and configure 2FA. This will prevent your account from being accessed and used in future phishing campaigns, even if your password is compromised.
- Enable the ‘spamheaders’ Zimlet: In Zimbra webmail, visit your Preferences, navigate to the Zimlets tab, and enable the spamheaders zimlet. This will help you see diagnostic headers and better evaluate suspicious messages.
What we’re doing
Our administration team is tracking these campaigns closely. We’re blocking domains, reporting abuse to registrars, and updating our filters in real time. But the most effective protection still comes from vigilant users who know what to look for.
We don’t send many emails specifically for our end-clients on our email platforms, so if you receive something claiming to be from us, and it seems off, trust your instinct and check with us.
And trust that we’re just as frustrated as you are.
Comments are currently closed.